Using SniffMaster for HTTPS Proxy Sniffing
Proxy sniffing is a traditional method for capturing packets, which requires setting up certificates and configuring the proxy. SniffMaster simplifies this process by automatically installing the necessary certificates. You only need to follow the prompts to trust the certificate on your iOS device and configure the proxy settings as instructed. If you accidentally close the prompt, click the help button to view the setup instructions.
Entering HTTPS Proxy Sniffing Mode
- Select the iOS device you want to capture packets from in the device list.
- In the feature area, select HTTPS Proxy Sniffing. Follow the on-screen prompts to install the configuration profile and set the proxy on your iOS device. If you’re sniffing on the local machine, the configuration will be done automatically; just follow the instructions.
iOS Device Setup
- Connect the Device: Connect the iOS device to the computer via USB. Ensure the device is unlocked and the screen is on.
- Trust the Computer: If this is the first time connecting the device to this computer, the phone will ask if you trust the computer. Tap Trust.
- Install iOS Driver: On Windows, when using SniffMaster for the first time, you may be prompted to install the required drivers. Follow the on-screen prompts to complete the installation. After installation, restart SniffMaster.
- Install Configuration Profile: If the device has not been used with SniffMaster before, the software will prompt you to install a configuration profile. Follow the instructions to install it on the iOS device.
- Configure Proxy: Ensure both the phone and computer are on the same local network. On your iOS device, go to the Wi-Fi settings, select the active Wi-Fi network, scroll to the bottom, tap Configure Proxy, choose Manual, and enter the address and port provided by SniffMaster. Save the settings.
Local Machine Sniffing Setup
If you are sniffing on your local Windows machine, SniffMaster requires administrator privileges for the first run. Right-click on SniffMaster and select Run as Administrator.
For Mac users, you will need to enter your system password when running SniffMaster for the first time.
Proxy Sniffing Features
- Start: Click this button to begin packet sniffing. Click it again to stop the capture after starting.
- Save: Save the captured data in HAR format for use with other software or for continued analysis.
- Filter: Use filters to exclude unwanted data, including filtering by URL, data type, request method, and more.
- Clear: Clear all captured data records.
- Delete: Delete selected data records.
- Help: Provides operational and usage guidance. If you accidentally close the software’s prompt, you can click this button to access help information.
- Table/Group View: Switch between grouped and table views of captured records, making it easier to delete and clean up data.
- Right-click Operations: Capture records support right-click options for deleting or copying URLs.
- Sort: Capture records can be sorted by multiple criteria by clicking on the table headers.
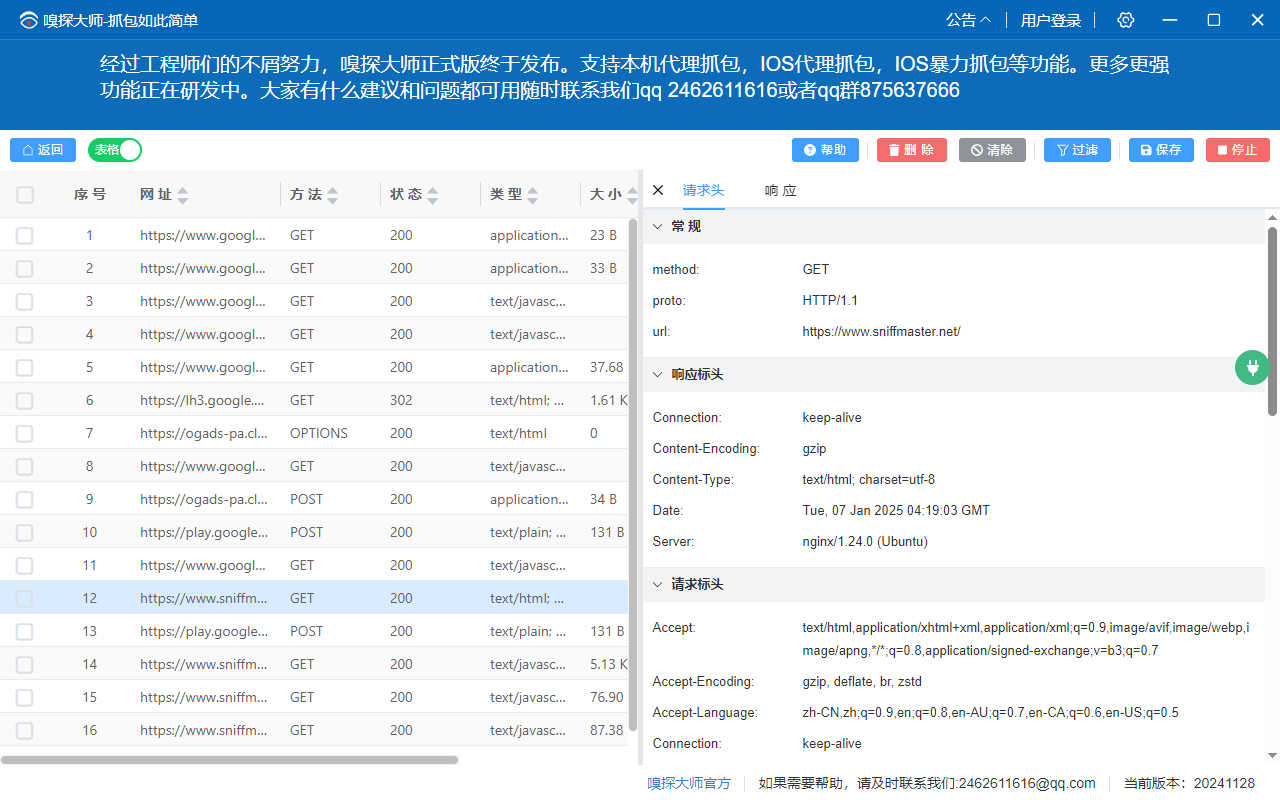
Interceptor and Modify Request/Response
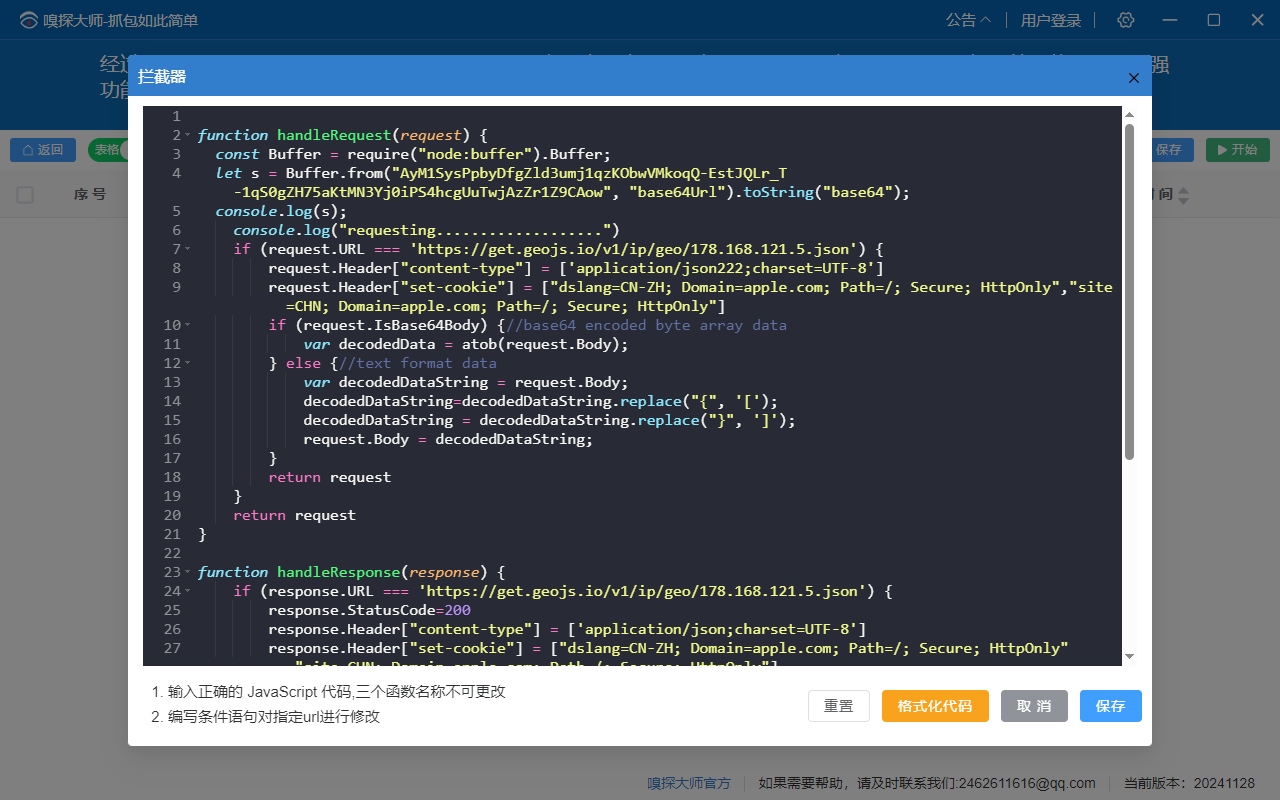
SniffMaster’s proxy sniffing supports intercepting and modifying requests and responses. You can write JavaScript code to modify headers, data, and URLs of requests and responses. Interceptor Detailed Tutorial. To open the interceptor interface, click the icon on the right side of the proxy sniffing screen, which resembles a plugin icon, and double-click the Interceptor Icon.
- Minimize: Minimize the interceptor interface to an icon.
- Maximize: Expand the interceptor interface to cover the entire software window.
- Clear: Clear the interceptor log messages.
- Interceptor Toggle: A control switch for enabling or disabling the interception code. When enabled, interception occurs; when disabled, no interception takes place.
- Edit Interceptor: Open the code editor for the interceptor logic, where you can write JavaScript code.
Interceptor Code Editor Interface
- iOS 抓包工具有哪些?全面盘点主流工具与功能对比分析
- iOS 抓包工具怎么选?开发者的实战经验与选择指南
- iOS 抓包工具有哪些?开发、测试与安全场景的实战选择
- 如何排查“链接 HTTPS”问题,工程化思路与iOS抓包流程
- 网站抓包,工程化抓取、分析与真机取证实战
- iOS 设备 抓包,iOS实机抓包到问题闭环的工程化实战
- Charles 抓不到包怎么办?一线工程师的排查与真机抓包流程
- Fiddler 抓不到包怎么办?从排查到替代方案的工程实战
- iOS 抓不到包怎么办?工程化排查与替代抓包方案(抓包/HTTPS/Charles代理/tcpdump)
- iOS HTTPS 抓包,从原理到落地排查的工程化方法(Charles / tcpdump / Sniffmaster)
- HTTPS 请求抓包,从原理到落地排查的工程化指南(Charles / tcpdump / Wireshark / Sniffmaster)
- iPhone HTTPS 抓包,从无法抓包到定位问题的流程(Charles/tcpdump/Wireshark/Sniffmaster)
- App HTTPS 抓包 工程化排查与工具组合实战
- iOS 手机抓包 App 怎么选与实战流程(抓包、HTTPS抓包、Charles、tcpdump、Wireshark)
- iOS 手机端抓包工具选型与实战攻略
- iOS 设备如何抓包,从入门到工程化排查的可执行指南(抓包、HTTPS抓包、Charles、tcpdump、Wireshark)
- iOS 抓包软件哪款更适合团队?工具职责、实战流程与替代方案解析
- iOS 抓包详细教程,一步步掌握 HTTPS 抓包、问题定位与工具组合(Charles / tcpdump / Wireshark / Sniffmaster)
- iOS 抓包工具有哪些,工具矩阵、职责分工与工程化选型建议
- 移动端 HTTPS 抓包实战,多工具组合分析与高效排查指南
- TCP 数据流分析全流程,从底层抓包到协议还原的实战指南
- iOS 免费抓包工具怎么选?从基础代理到多协议分析的完整指南
- iOS 抓包全流程指南,HTTPS 抓包、TCP 数据流分析与多工具协同的方法论
- iOS App HTTPS 抓包实战:从 TLS 分析到多工具协同的完整解决方案
- Fiddler 抓包失败怎么办?从代理排查到 TCPTLS 分析的完整解决方案
- Charles 抓包失败怎么办?从代理排查、TLS 分析到多工具协同的完整方案
- iPhone 抓包软件怎么选?从代理抓包到 TCP 数据流分析的完整实践指南
- iOS 抓包实 从 HTTPS 调试到 TCP 数据流分析,一套适用于所有场景的完整方案
- iOS 应用抓包完整指南,HTTPS 调试、协议分析与多工具协同的工程化流程
- Mac 抓包软件怎么选?从 HTTPS 调试、TCP 数据流分析到多工具协同的完整抓包方案
- iOS APP 抓包全流程解析,HTTPS 调试、网络协议分析与多工具组合方案
- Fiddler 抓不到包怎么办?从 HTTPS 调试到 TCP 分析的完整排查方案
- Charles 抓不到包怎么办?从 HTTPS 分析到 TCP 抓包的全流程排查指南
- iOS 抓不到包怎么办?从 HTTPS 解密、QUIC 排查到 TCP 数据流分析的完整解决方案
- iPhone 抓包工具怎么选?从 HTTPS 调试、TCP 数据流分析到多工具协同的完整方案
- 移动端抓包完整指南,HTTPS 调试、TCP 数据流分析与多工具协同方案
- iOS HTTPS 抓包全流程 TLS 分析、代理排查与底层数据流捕获方案
- iOS 手机端抓包工具怎么选?HTTPS 调试、TCP 数据流分析与多工具协同的完整实践指南
- Fiddler 抓不到包怎么办?从代理排查到 TCP 数据流分析的多工具联合解决方案
- iOS 手机抓包软件怎么选?HTTPS 调试、TCP 数据流分析与多工具组合的完整实践
- Charles 抓不到包怎么办?从 HTTPS 代理排错到底层数据流补抓的完整解决方案
- TCP 抓包分析实战,从三次握手到自定义协议解析的完整方法
- Web 抓包完整实践指南,从浏览器网络调试到底层数据流捕获的全流程方案
- HTTPS 抓包软件深度解析,从代理解密到底层数据流捕获的多工具协同方案
- Fiddler 抓不到包怎么办?HTTPS 抓包失败、QUIC 流量绕过与底层补抓方法全流程解析
- iPhone HTTPS 抓包实战指南,移动端加密流量分析、代理解密失败排查与底层数据流捕获
- Python 抓包工具全面解析,从网络监听、协议解析到底层数据流捕获的多层调试方案
- HTTPS 错误解析全指南,从 TLS 握手失败、证书链异常到抓包定位策略
- HTTPS 端口深度解析,443 并不是唯一入口,理解 TLS 流量行为与抓包策略
- HTTPS 双向认证抓包难点解析,TLS Mutual Authentication 行为、抓包失败原因与底层数据流分析方法
- App HTTPS 抓包实战解析,从代理调试到真实网络流量观察的完整抓包思路
- Engineering Troubleshooting and Tool Combination for App HTTPS Packet Capture
- iOS 抓包工具实战指南,从代理到数据流,全流程工具分工解析
- HTTPS DDoS 排查 异常流量到抓包分析
- 数据流抓包实战,在HTTP 之外看清真实网络通信
- HTTPS 抓包乱码这件事,通常不是编码问题那么简单
- 关于 iphone抓包软件,我是在什么时候真正意识到选好工具很重要
- iOS App HTTPS 抓包在实机环境下的常见问题
- iOS 上架的过程,结合Xcode、Fastlane和开心上架
- 抓包工具对比,多种抓包工具在不同阶段的实际作用
- HTTP 协议详解,HTTP 协议在真实运行环境中的表现差异
- Fiddler 抓不到包怎么办?抓不到包时常见的判断误区
- TCP 抓包分析在复杂网络问题中的作用,从连接和数据流层面理解系统异常行为
- Web 抓包在浏览器、代理、设备侧等不同层面的作用
- 抓包工具有哪些?代理抓包、数据流抓包、拦截转发工具
- iOS 抓包工具在不同场景的实际作用
- iOS app 为什么会抓不到包,不是配置没配好那么简单
- python 抓包在实际项目中的合理位置,结合代理抓包、设备侧抓包与数据流分析
- Charles 抓不到包怎么办?Charles 抓不到包时的常见误判
- iPhone HTTPS 抓包在真机环境下面临的常见问题
- 工程师必看,Mac 抓包软件的使用场景
- iOS 抓包工具有哪些?不同类型的抓包工具可以做什么
- iOS 安装了证书,HTTPS 还是抓不到
- iOS App 中 SSL Pinning 场景下代理抓包失效的原因
- 在 Windows 环境下抓取 iOS App 网络数据的过程
- iOS App的tcp、udp数据包抓取在实际开发中的使用方式
- 在 iPhone 上进行 iOS 网络抓包的实践经验
- 在调试中,如何使用抓包大师拦截器对网络请求和网络应答进行拦截修改
- 常见 iOS 抓包工具的使用方式与组合思路
- 有没有在 iOS 直接抓包 的App?
- 如何在苹果手机上面进行抓包?iOS代理抓包,数据流抓包
- HTTPS 协议和 TLS 握手过程详解,iOS 实际抓包调试
- Charles 抓不到包怎么办?iOS 调试过程中如何判断请求路径
- iOS 抓包工具实战实践指南,围绕代理抓包、数据流抓包和拦截器等常见工具
- iOS App 抓不到包时的常见成因与判断思路,结合iOS 调试经验
- iOS App 抓不到包怎么办?结合tcp数据流抓包、HTTPS 代理抓包等方便
- 设置了 SSL Pinning 与双向 TLS 验证要怎么抓包
- iOS 抓包绕过 SSL 证书认证, HTTPS 暴力抓包、数据流分析
- Mac 抓包软件有哪些?Charles、mitmproxy、Wireshark和Sniffmaster哪个更合适
- Fiddler 抓不到包怎么办?代理是否生效、HTTPS 解密状态、iOS App 通信
- iPhone 网络调试的过程,请求是否发出,是否经过系统代理,app 绕过代理获取数据
- 只抓某个 App 的网络请求,把无关流量排除在 iOS 调试视野之外
- iOS 抓包中请求与响应拦截器,修改请求与响应数据
- Flutter iOS App 怎么抓包,代理抓包、HTTPS 拦截验证
- 抓包工具推荐 2026,网络调试、代理抓包、请求拦截
- HTTPS 代理失效,启用双向认证(mTLS)的 iOS 应用网络怎么抓包调试
- 傻瓜式 HTTPS 抓包,简单抓取iOS设备数据
- 常见 iOS 抓包工具的使用,从代理抓包、设备抓包到数据流抓包
- iOS 如何绕过 ATS 发送请求,iOS调试
- iOS App HTTPS 抓包,从系统代理到设备上直接抓包
- 使用 Sniffmaster TCP 抓包和 Wireshark 网络分析
- HTTPS 端口解析,除了 443 端口还有哪些
- 在 Windows 环境下抓取 iPhone 网络流量的操作流程
- 开始使用
- HTTPS暴力抓包
- 数据流抓包
- 代理抓包
- 嗅探大师常见问题
- 嗅探大师拦截器详细教程
- 嗅探大师android版
- Start
- Crack HTTPS Sniffing
- Capture iOS TCP Packets
- Interceptor Guide